$9 Million Heist: A Deep Dive into the Yearn yETH Pool Vulnerability
This article provides a comprehensive analysis of the recent $9 million exploit on Yearn's yETH Weighted Stableswap Pool. It explains the root cause of the vulnerability, the attack methodology, and the implications for blockchain security.
$9 Million Heist: A Deep Dive into the Yearn yETH Pool Vulnerability
On December 1, 2025, the decentralized finance (DeFi) space witnessed a significant breach when Yearn, a leading decentralized yield aggregation protocol, was exploited for approximately $9 million. The SlowMist security team has conducted an exhaustive investigation to uncover the intricacies of this attack, the underlying vulnerabilities, and lessons for the broader blockchain ecosystem.
Background
Yearn's yETH Weighted Stableswap Pool aggregates various Ethereum liquid staking derivatives (LSTs) to provide users with an efficient automated market maker (AMM) pool. By depositing diverse LST assets, liquidity providers receive yETH tokens representing their shares in the pool.
Central to this mechanism are two concepts:
- Virtual Balance (vb): Calculated as the asset balance multiplied by its rate from respective rate providers.
- Total Supply (variable D): Represents the total LP token supply when the pool is balanced.
Maintaining a 1:1 peg between tokens and underlying assets relies on an intricate formula balancing virtual balances and supply.
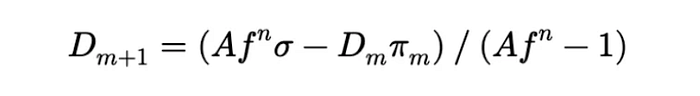
The Vulnerability: Root Cause Explained
At the heart of this exploit lies a critical flaw within the _calc_supply function used in the yETH Weighted Stableswap Pool contract. This function recalculates the LP token supply based on pool assets and their virtual balances.
Core Issue:
- The function performs unsafe mathematical operations, lacking proper overflow and underflow checks.
- Specifically, during supply recalculations, it uses an unchecked subtraction (
unsafe_sub) leading to underflow. - This triggers incorrect computations of the virtual balance product (
vb_prod), which can drop to zero. - Once
vb_prodbecomes zero, the function's iterative calculations produce inflated supply values, enabling attackers to mint excessive LP tokens illegitimately.
In simpler terms, the exploit allows an attacker to manipulate internal pool calculations to their advantage, creating tokens out of thin air.
Anatomy of the Attack
The attacker exploited the vulnerability via a multi-step strategy:
- Flash Loan Acquisition: Leveraging a flash loan, the attacker borrowed large amounts of LST assets including wstETH, rETH, WETH, and others.
- Liquidity Manipulation Cycles: They repeatedly removed and added liquidity in a carefully crafted sequence.
- By selectively adding back fewer assets during re-adding phases, they manipulated internal virtual balances.
- These cycles forced the
vb_prodvalue to zero due to underflows in supply calculations.
- Minting Inflated LP Tokens: With
vb_prodat zero, the attacker could mint an excessive amount of yETH tokens. - Restoring
vb_prod: They restored the virtual balance product to a non-zero value via a zero-amount liquidity removal, further masking manipulations. - Redeeming and Draining the Pool: Exploiting the inflated supply, the attacker redeemed LP tokens for actual assets, draining the pool.
- Overflow Exploit: Adding minimal ('dust') liquidity caused an overflow in multiplication during supply calculation, resulting in astronomical LP token minting.
- Cash Out: The attacker sold the illicitly minted yETH tokens on AMMs and repaid the flash loans, netting roughly $9 million.
This complex but precise orchestration highlights the risks of unchecked arithmetic and state manipulations in DeFi contracts.
Behind the Screens: Technical Deep Dive
The key vulnerability centered on the equation:
$$ s' = \frac{l - s \times r}{d} $$
Where:
- s is the supply,
- r is the virtual balance product,
- l combines amplification and virtual balances,
- d is a constant adjusted for amplification.
During iteration, the unsafe_sub operation meant when s * r exceeded l, an underflow occurred, yielding a small value instead of an error.
Consequently, when the virtual balance product r' was recalculated as:
$$ r' = r \times \left(\frac{s'}{s}\right)^8 $$
it rounded down to zero. This poisoned all future calculations, allowing the attacker to inflate the supply drastically.
Aftermath and Recovery
Blockchain analytics via MistTrack pinpointed the attacker’s movements:
- Initial ETH transfers from privacy-focused mixers like Railgun and Tornado Cash.
- Consolidation of stolen assets into specific “hot” wallets.
- Partial recovery by Yearn involved burning a portion of the stolen pxETH tokens.
The attacker’s sophisticated methods emphasize the need for robust on-chain monitoring, AML practices, and rapid incident response protocols.
Key Takeaways for DeFi Projects
- Thorough Edge Case Testing: Extensive audits should include testing on extreme input values and states to uncover hidden overflow/underflow bugs.
- Safe Arithmetic Practices: Utilize secure math libraries (like OpenZeppelin's SafeMath) with active overflow checks.
- Immutable Contract Constraints: Whenever possible, restrict mutability of critical state variables or introduce sanity checks.
- Rate Provider Integrity: Properly verify and secure external data feeds (oracles) to prevent rate manipulation.
- Continuous Monitoring: Employ real-time detection systems for suspicious contract interactions.
Conclusion
The Yearn yETH pool exploit serves as a stark reminder of the perils lurking in the complexities of DeFi smart contracts. Even minor oversights in mathematical operations can cascade into catastrophic financial losses. As DeFi continues to evolve, prioritizing meticulous security, rigorous testing, and swift vulnerability patching remain paramount to safeguarding users’ assets and trust.
Further Reading
Written by the SlowMist Security Research Team