A Cautionary Tale: How a Next.js Server Was Compromised by Crypto-Mining Malware and What You Can Do
An in-depth analysis of a crypto-mining malware attack on a Next.js server, highlighting the technical details, root causes, forensic findings, and critical security lessons for developers using React/Next.js with Docker.
A Cautionary Tale: How a Next.js Server Was Compromised by Crypto-Mining Malware and What You Can Do
Recently, Eduardo Borges shared a harrowing experience on X (formerly Twitter) about how his Next.js server was hacked and turned into a crypto-mining botnet node. This incident exposes critical vulnerabilities affecting React/Next.js developers deploying applications with Docker, and underscores the importance of container security. In this post, we'll dissect this attack's anatomy, the root cause, forensic discoveries, its financial impact, and key takeaways to prevent a similar fate.
The Initial Alarm: Hetzner's Netscan Detected Notification
Eduardo woke up to an alarming email from his hosting provider, Hetzner, stating "Netscan Detected." His server IP had been blocked because it was identified as part of a botnet launching attacks. What followed was an intense investigation revealing that his server was secretly mining cryptocurrency.
Anatomy of the Attack
1) Symptoms and Detection
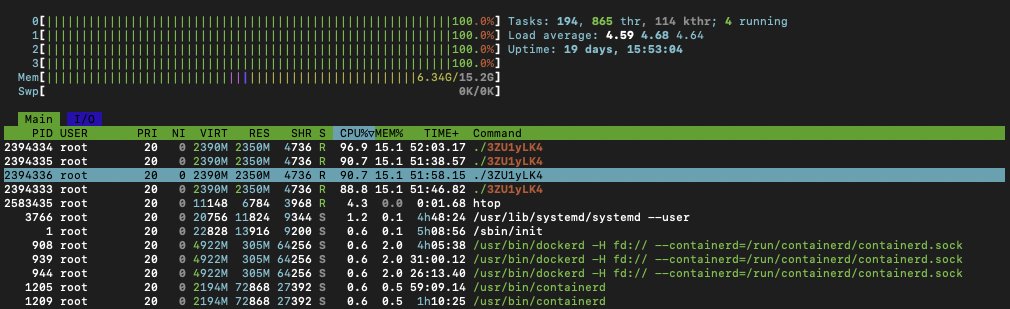
Using htop, Eduardo observed:
- CPU usage spiking at over 361%
- A suspicious process named
./3ZU1yLK4consuming resources - Outgoing connections to an IP address in the Netherlands
His Next.js application was offline; the server was hijacked to mine crypto.
2) Malware Characteristics
- Not a typical SSH brute-force.
- Malware resided inside the Next.js Docker container.
- It disguised itself as legitimate services, renaming to
nginxsandapachesto appear as web servers. - Included a "killer" script to eliminate competing miners, asserting dominance over infected hosts.
3) Root Cause Analysis
- Likely exploited a recent vulnerability: React/Next.js CVE-2025-66478. Despite running Next.js version 15.5.4 behind Cloudflare DNS with recent patches, the fix was ineffective.
- The critical error: the Next.js Docker container ran as
rootuser. Coolify deployments using Nixpacks default to root unless explicitly changed. - As root, malware installed persistent components such as cron jobs and systemd services, surviving reboots and infecting the entire server.
4) Forensic Revelations
Executing docker diff on the container revealed:
/tmp/apaches.sh: the malware installation script/var/spool/cron/root: cron jobs for persistence/c.json: configuration file containing the hacker's crypto wallet details
5) Remediation Steps
- Shut down and removed the infected container.
- Thoroughly cleaned the server environment.
- Extracted malware for further analysis.
The Crucial Fix: Dockerfile User Configuration
Developers deploying Node/Next.js apps must not run containers as root. Update your Dockerfile to include:
RUN adduser --system nextjs
USER nextjs
Verify running containers with:
docker exec <container_id> id
If output shows uid=0(root), you risk an easy path for attackers.
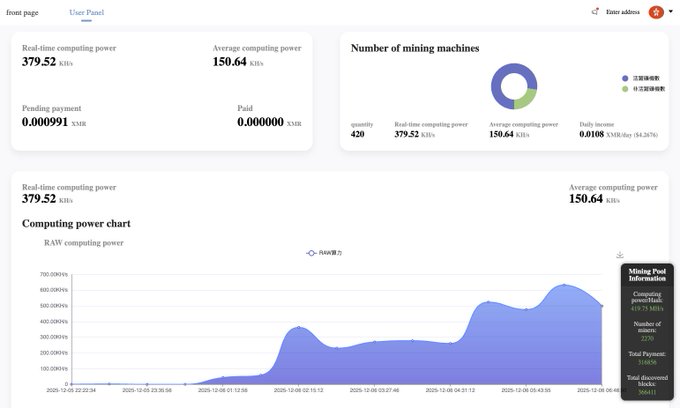
6) Financial Impact: Tracing the Crypto Wallet
- The malware mined Monero (XMR) and sent earnings to address:
831abXJn8dBdVe5nZ*** - Mining pool:
auto.c3pool.org - Botnet size: 415 infected cloud servers all mining simultaneously
- As of Eduardo's discovery, earnings were about $4.26/day — a small but potentially scalable amount
7) Attack Scale and Attribution
- Eduardo discovered this botnet was widespread, burning CPU cycles on hundreds of cloud servers.
- Malware code contained comments in Chinese, hinting at possible origin.
Key Lessons and Best Practices
- Never run production containers as root. Always specify a non-root user.
- Keep dependencies and frameworks patched. Stay updated on CVE mitigations.
- Monitor server resource usage closely. High CPU without apparent reason can be a sign of compromise.
- Review container changes with
docker diffperiodically. Unexpected file additions or modifications warrant investigation. - Use layered defenses: behind Cloudflare, network firewalls, security groups.
- Back up critical data and use immutable infrastructure to rebuild when suspicious activity is detected.
Conclusion
Eduardo Borges's experience serves as a stark warning for developers leveraging Next.js and Docker. Security oversights, especially around user permissions, can quickly escalate into severe server compromises enabling attackers to profit at your expense. By following the outlined precautions and remediation steps, you can fortify your deployments against such threats.
Stay vigilant and safe!
References
-
Original thread by Eduardo Borges: Link
-
React/Next.js CVE-2025-66478 Details