Deep Dive into the yETH Exploit: A Multifaceted Examination
An analytical exploration of the sophisticated yETH exploit, focusing on its mechanics and implications.
Deep Dive into the yETH Exploit: A Multifaceted Examination
In the ever-evolving landscape of decentralized finance (DeFi), few events have illustrated the potential for sophisticated attacks as vividly as the recent yETH exploit. After diving into the technical intricacies of this event, it's evident that it is one of the most complex attacks witnessed in the DeFi space. Alarmingly, many accounts of the incident have misunderstood various aspects of the attack. This blog post aims to clarify those misconceptions and provide developers and security researchers with valuable insights into the exploit.
Understanding the Hybrid AMM Curve
Before delving into the specifics of the exploit, it's crucial to grasp the underlying mechanics of the yETH protocol. The yETH pool operates on a hybrid mechanism, combining features of both constant product and constant sum market-making curves. Familiarity with Uniswap's constant product model may serve well here; it adjusts prices based on reserve levels, while the constant sum model maintains constant prices between tokens, independent of reserves.
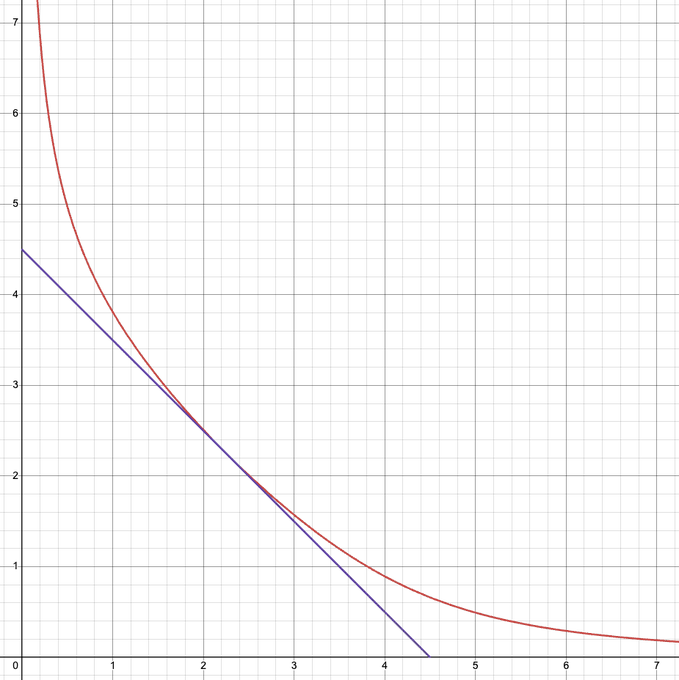
The hybrid curve utilized by yETH behaves like a constant sum curve when token reserves are balanced, ensuring constant price stability. Conversely, when reserves become imbalanced, it transitions to a constant product model. This characteristic proves advantageous for asset pools of equal value, as it reduces price sensitivity to reserve changes. Below is a visual representation of these curves:
Red: Constant Product | Green: Constant Sum | Blue: yETH Hybrid
The First Bug: Disruption of the Invariant
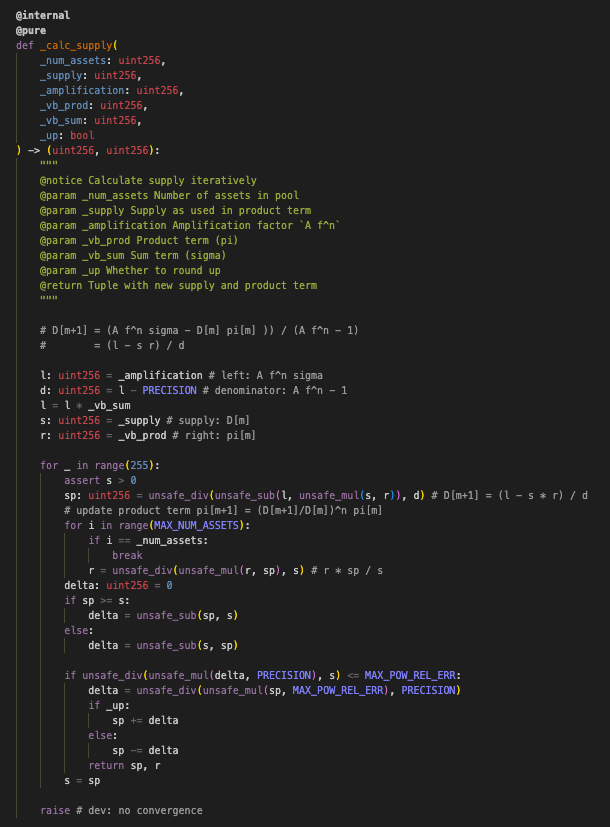
Focusing on the heart of the protocol, we examine the _calc_supply function. This function leverages an iterative approximation to compute a new supply along with the constant product term in each iteration until sufficient precision is attained.
Iterative approximation process
The constant product term (r) is recalculated during every iteration, defined as the product of the current value with the new supply, then divided by the previous supply (r * sp / s). If, however, the supply decreases drastically during any iteration, this term can round down to zero. The lack of a revert mechanism in this scenario causes a cascading failure: subsequent iterations retain a zero constant product term. Consequently, the hybrid constant product/constant sum curve collapses into merely a constant sum curve.
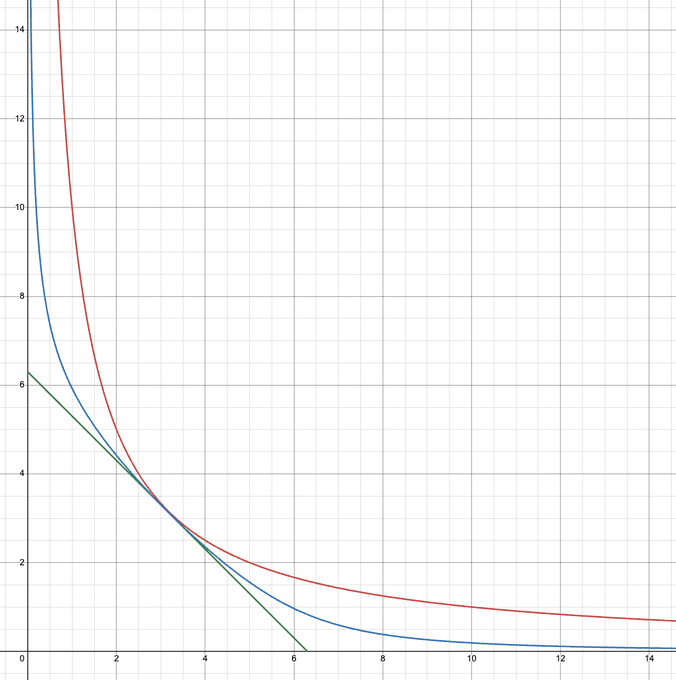
To illustrate the implications of this shift, consider the graphs below:
Intended Curve (Red) vs Constant Sum Curve (Purple)
As liquidity is added or removed, these two curves mint or burn differing amounts of Liquidity Provider (LP) tokens, particularly when reserves are imbalanced. The attacker exploited this anomaly, transitioning between the curves by triggering the zero constant product term. This method allowed them to receive more LP tokens than intended, which were later corrected, enabling them to withdraw more tokens than they initially deposited. The result? A staggering profit of approximately $8 million.
The Second Bug: Unexpected Underflow
But wait, the exploit didn't end there. Once the pool was drained, the attacker capitalized on another bug that enabled them to extract even more funds. When attempting to deposit certain minimal amounts after the pool was emptied, the accounting variables were left in an unusual state, resulting in unexpected side effects.
As illustrated in the _calc_supply function, we calculate supply using the expression:
(l - s * r) / d. Due to the use of unchecked math in a peculiar accounting state, it is possible for s * r to exceed l, resulting in an underflow. This bug was exploited by the attacker who deposited a series of amounts: [1, 1, 1, 1, 1, 1, 1, 9], ultimately minting approximately 2.6 * 10^56 yETH LP tokens.
The attacker executed a swap on the yETH/WETH pool, further draining it of its WETH reserves for an additional profit close to $1 million.
Conclusion
The yETH exploit serves as a stark reminder of the vulnerabilities that can arise from even highly sophisticated, well-designed protocols. By exploiting a combination of an AMM invariant and an underflow, the attacker executed a complex orchestration leading to the complete draining of the yETH pool and affected another pool containing the LP token. Critically, all actions transpired within a single transaction, eliminating any potential chance for recovery.
In reviewing various analyses of this exploit, I've found that many fail to grasp some aspect of the attack’s intricacies. A comprehensive understanding of such sophisticated exploits is rare, emphasizing the need for continuous education and vigilance among developers and security researchers in the blockchain space. This incident not only highlights the fragility of DeFi but also offers valuable lessons for future protocol design and security.